Trivial Flag Transfer Protocol
Overview
Points: 90 Category: Forensics
Description
Figure out how they moved the flag.
Hints
- What are some other ways to hide data?
Approach
When looking at the packet capture using Wireshark, I noticed there were a lot of files. For some reason I thought TFTP wasn't a legit protocol and was instead, something Pico made up but uhhhh I looked into it after solving this question lol.
To extract the files watch this video, on Wireshark:
File > Export Objects > TFTP
which shows all the files recorded in the packet capture
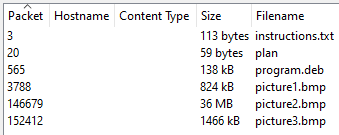
Click "Save All" to save them.
The files included instructions.txt, plan, program.deb, picture1.bmp, picture2.bmp, and picture3.bmp. Let's analyze each of them individually.
instructions.txt
Here are the contents of instructions.txt:
GSGCQBRFAGRAPELCGBHEGENSSVPFBJRZHFGQVFTHVFRBHESYNTGENAFSRE.SVTHERBHGNJNLGBUVQRGURSYNTNAQVJVYYPURPXONPXSBEGURCYNA
Wow! Encrypted data! My first thought was a substitution of some sort. It turned out to be ROT13
TFTPDOESNTENCRYPTOURTRAFFICSOWEMUSTDISGUISEOURFLAGTRANSFER.FIGUREOUTAWAYTOHIDETHEFLAGANDIWILLCHECKBACKFORTHEPLAN
I actually thought this was nonsense at first so I'll add in the spaces for you XD
TFTP DOESNT ENCRYPT OUR TRAFFIC SO WE MUST DISGUISE OUR FLAG TRANSFER. FIGURE OUT A WAY TO HIDE THE FLAG AND I WILL CHECK BACK FOR THE PLAN
Check back for the plan? Ok onto the the plan!
plan
Here are the raw contents of plan:
VHFRQGURCEBTENZNAQUVQVGJVGU-QHRQVYVTRAPR.PURPXBHGGURCUBGBF
Once again, it is encrypted using ROT13. Here's the decrypted message
IUSEDTHEPROGRAMANDHIDITWITH-DUEDILIGENCE.CHECKOUTTHEPHOTOS
Here's some spaces:
I USED THE PROGRAM AND HID IT WITH-DUE DILIGENCE. CHECK OUT THE PHOTOS
Hmmm "used the program"
program.deb
I opened program using 7-zip and found many files that seemed to all point to steghide.
pictures



In all honesty the actual content of the pictures themselves have absolutely nothing to do with anything. I just want to say the huge size of picture2.bmp really threw me off.
steghide and finally solving
There's a part on steghide's README titled "Quick-Start" that explains how to use it. I used the command steghide info picture3.bmp (no particular reason to start with 3, in this case it's just that picture3 is the one that had all the juicy info like the flag) and it prompted me for a passcode. I was going to bruteforce the passcode I remembered the contents of plan:
IUSEDTHEPROGRAMANDHIDITWITH-DUEDILIGENCE.CHECKOUTTHEPHOTOS
ANDHIDITWITH-DUEDILIGENCE
What if "DUEDILIGENCE" was the password the flag is hidden with? With "DUEDILIGENCE" as the password, steghide revealed there's a flag.txt hidden inside picture3. Using steghide extract -sf picture3.bmp and "DUEDILIGENCE" as the password, flag.txt was extracted.
Flag
picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}